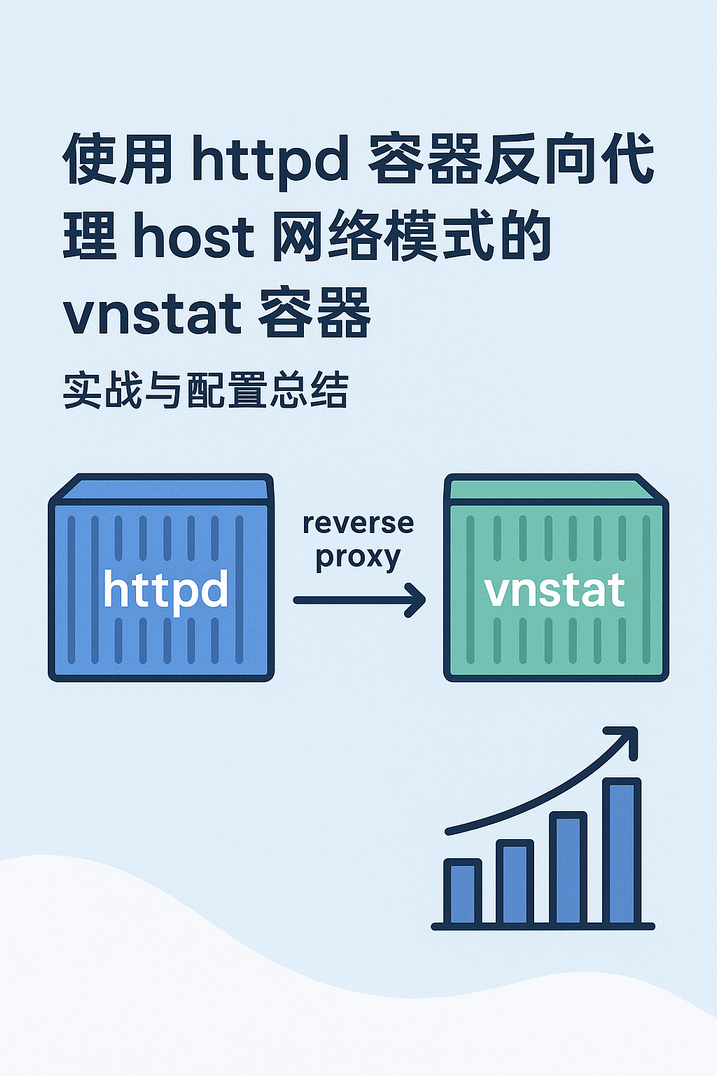
在使用 Docker 构建可视化网络监控系统时,一个常见的需求是通过 Web 服务(如 Apache http…
Racknerd AMD Ryzen Windows VPS 推荐
目前Racknerd AMD Ryzen Windows 还是比较划算的,大致参数:KVM虚拟,AMD Ryz…
ipv6 list
The ipv6 TV list is extracted from the ipv6 channels of…
openmediavault(6.0) acme get Let’s encrypt SSL certificate for dynu ddns
1 Introduction Acme.sh is a free project that can get f…
Using Let’s Encrypt Certification for Synology Nas Systems With dynu as DDNS Provider and auto-renew it (updated 5-26-23)
When we use the Synology Nas system it is convenient to…
受保護的內容: 主路由openwrt旁路由openwrt设置方案
受密碼保護的文章不會產生內容摘要。
js splice
//刪除位置2前面的元素,加入元素 var arr = new Array(6)arr[0] = “…
使用 Promise
Promise 是一個表示非同步運算的最終完成或失敗的物件。由於多數人使用預建立的 Promise,這個導覽會…
docker modify ip
First,stop the containers running: docker stop t1node t…